When managing your server, security is paramount. One of the most effective ways to secure your Linux VPS or dedicated server is by replacing traditional password logins with SSH key authentication. Unlike passwords that can be brute-forced or stolen, SSH keys offer a more secure and convenient way to authenticate.
In this guide, we’ll walk you through what SSH keys are, how they work, and how to set them up on your server.
🔑 What is SSH Key Authentication?
SSH (Secure Shell) is a protocol used to securely connect to remote servers. Instead of typing a password every time, SSH key authentication uses a pair of cryptographic keys:
-
Private key → stays on your local computer (keep it safe).
-
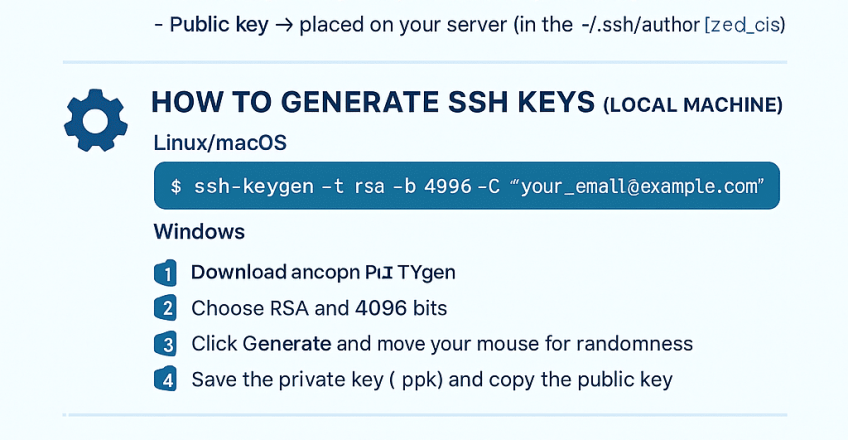
Public key → placed on your server (in the
~/.ssh/authorized_keysfile).
When you connect, the server verifies that the private key matches the stored public key. If it does, access is granted—no password needed.
✅ Benefit: This makes your server far less vulnerable to brute-force attacks.
⚙️ How to Generate SSH Keys (Local Machine)
First, generate your SSH key pair on your local machine.
On Linux/macOS:
This will:
-
Create a 4096-bit RSA key pair.
-
Save it to
~/.ssh/id_rsa(by default). -
Prompt you to set a passphrase for extra protection.
On Windows:
If you’re using PuTTYgen:
-
Download and open PuTTYgen.
-
Choose RSA and 4096 bits.
-
Click Generate and move your mouse for randomness.
-
Save the private key (
.ppk) and copy the public key.
📥 Adding the Public Key to Your Server
Now, copy your public key to the server.
Using ssh-copy-id (Linux/macOS):
Manually:
-
SSH into your server:
-
Create a
.sshdirectory (if it doesn’t exist): -
Add your public key:
Paste your public key inside.
-
Set permissions:
🔒 Disabling Password Authentication
Once SSH key login works, disable password-based login for extra protection.
-
Open SSH config file:
-
Find and change:
-
Restart SSH:
Now, only SSH keys can be used to log in.
✅ Advantages of SSH Key Authentication
-
Stronger security than passwords.
-
Protects against brute-force login attempts.
-
More convenient (no need to type password every time).
-
Can be combined with passphrases + 2FA for maximum security.
🌍 Related Resources
-
How to Configure UFW Firewall on Ubuntu VPS (Sternhost Guide)
-
Sternhost VPS Hosting Plans (Secure hosting with SSH support)
📌 Conclusion
SSH key authentication is one of the simplest yet most powerful security measures you can take for your server. By setting it up, you significantly reduce the risk of unauthorized access and make managing your VPS more convenient.
If you’re running your server with Sternhost VPS Hosting, you already have the tools needed to implement SSH key authentication in minutes. Secure your server today—because safety should never be optional.


